Secure Hash Algorithm (SHA-1) was designed by National Security Agency (NSA) during 1995 as part of the Digital Signature Standard and mainly used to verify the authenticity of the digital content. SHA-1 is a cryptographic hash function which produces 160 bit hash value known as a Message Digest. It is used in several security applications and protocols, including TLS, SSL, PGP, SSH, S/MIME, and IPsec.
The theoretical flaws of SHA-1 was first identified in 2005 which would break the algorithm using Collision attacks. But despite these warnings SHA-1 was widely used as a powerful cryptographic algorithm over the last decade. Google researchers on 23rd February 2017 announced the First Practical Collision Attack on SHA-1.
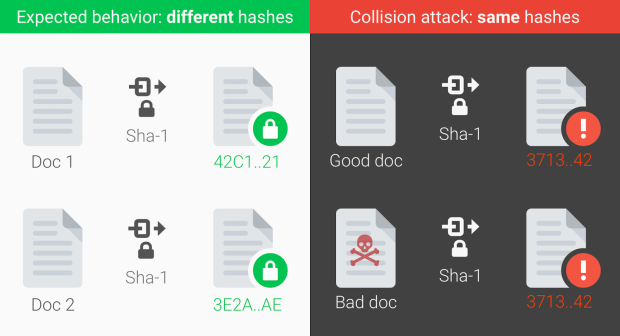
SHA-1 hash function converts an input message to a hash value called as a digital fingerprint for the given message which is rendered as hexadecimal numbers. By checking the hash, the authenticity and integrity of the message can be easily verified. Each message creates a unique hash value, if the hashes match then the messages will also match. This helps to verify the messages without exposing the message itself.
Collision attacks happens when same digital fingerprint is created for two different messages i.e. the legitimate message and malicious message. This could allow the attackers to forge digital signatures and break communications encoded with SHA-1. On the grounds of collision attacks on SHA-1, it is not secure to use it for digital signatures, file integrity, and file identification purposes.
As a proof of concept, the researches have used two different PDF’s with totally different content and have the same SHA-1 hash. As pointed out by one of the researchers, this attack required over 9,223,372,036,854,775,808 SHA-1 computations, This took the equivalent processing power as 6,500 years of single-CPU computations and 110 years of single-GPU computations. Google is planing to release the proof of concept code within 90 days. So its high time to move to safer standards before real world attacks happen.
SHA-1 collision attacks have not affected the HTTPS-protected websites as the certificate authorities are no longer allowed to use SHA-1 to sign TLS certificates.